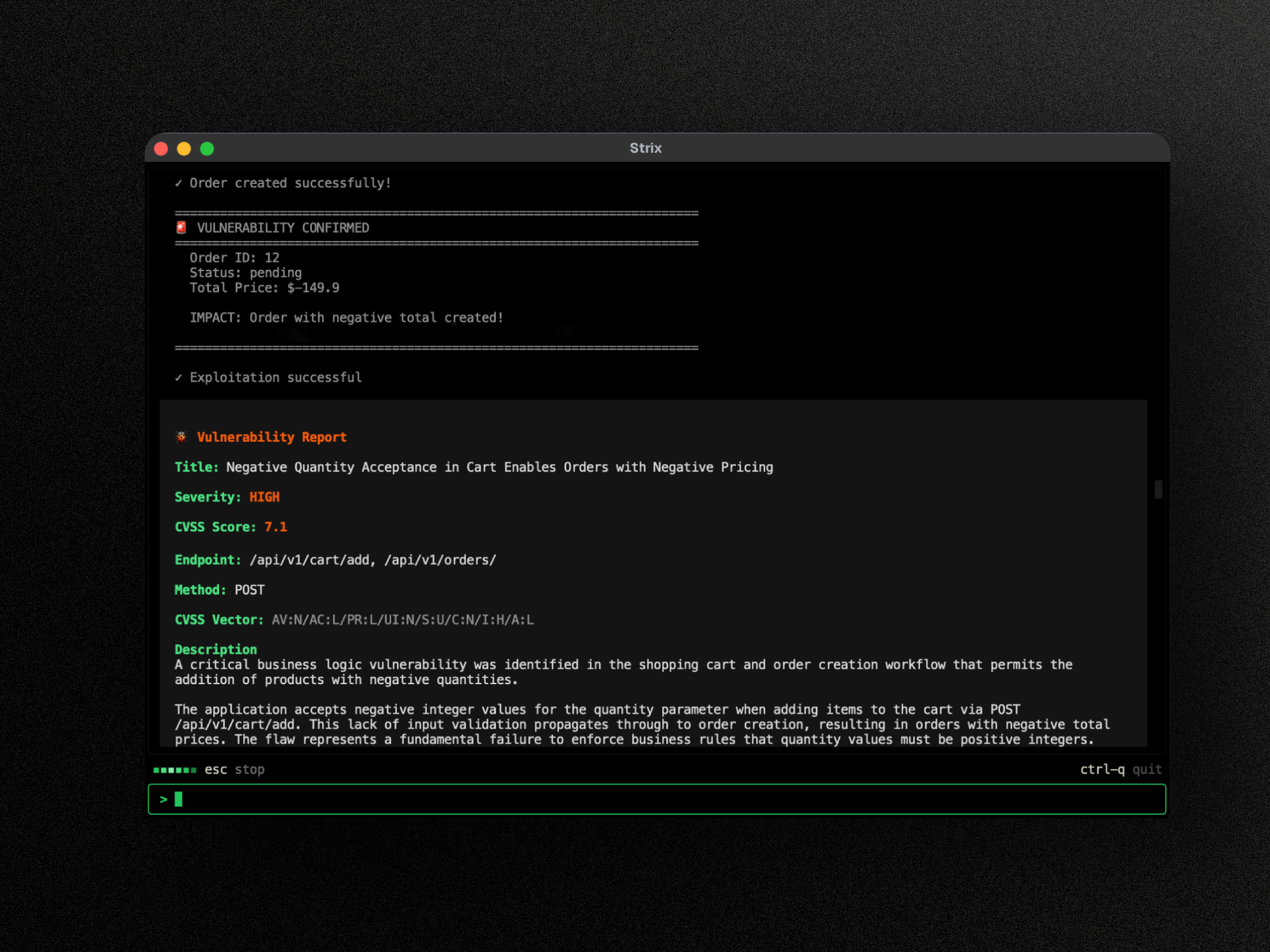
Quick Start
Install and run your first scan in minutes.
CLI Reference
Learn all command-line options.
Tools
Explore the security testing toolkit.
GitHub Actions
Integrate into your CI/CD pipeline.
Use Cases
- Application Security Testing — Detect and validate critical vulnerabilities in your applications
- Rapid Penetration Testing — Get penetration tests done in hours, not weeks
- Bug Bounty Automation — Automate research and generate PoCs for faster reporting
- CI/CD Integration — Block vulnerabilities before they reach production
Key Capabilities
- Full hacker toolkit — Browser automation, HTTP proxy, terminal, Python runtime
- Real validation — PoCs, not false positives
- Multi-agent orchestration — Specialized agents collaborate on complex targets
- Developer-first CLI — Interactive TUI or headless mode for automation
Security Tools
Strix agents come equipped with a comprehensive toolkit:| Tool | Purpose |
|---|---|
| HTTP Proxy | Full request/response manipulation and analysis |
| Browser Automation | Multi-tab browser for XSS, CSRF, auth flow testing |
| Terminal | Interactive shells for command execution |
| Python Runtime | Custom exploit development and validation |
| Reconnaissance | Automated OSINT and attack surface mapping |
| Code Analysis | Static and dynamic analysis capabilities |
Vulnerability Coverage
| Category | Examples |
|---|---|
| Access Control | IDOR, privilege escalation, auth bypass |
| Injection | SQL, NoSQL, command injection |
| Server-Side | SSRF, XXE, deserialization |
| Client-Side | XSS, prototype pollution, DOM vulnerabilities |
| Business Logic | Race conditions, workflow manipulation |
| Authentication | JWT vulnerabilities, session management |
| Infrastructure | Misconfigurations, exposed services |
Multi-Agent Architecture
Strix uses a graph of specialized agents for comprehensive security testing:- Distributed Workflows — Specialized agents for different attacks and assets
- Scalable Testing — Parallel execution for fast comprehensive coverage
- Dynamic Coordination — Agents collaborate and share discoveries